Multifactor authentication (MFA) adds an extra layer of security by requiring more than just a password to log in. Most commonly, this is done by entering a Time-based One Time Password (TOTP) generated by an authentication app on your phone. This helps protect your account even if your password was guessed, stolen, or leaked, by ensuring that only someone with access to your registered device can log in.
| Table of Contents |
|---|
Setting Up MFA
Before you begin, make sure your authenticator is ready. If you need help on TOTP authenticators, see section 5 in this page.
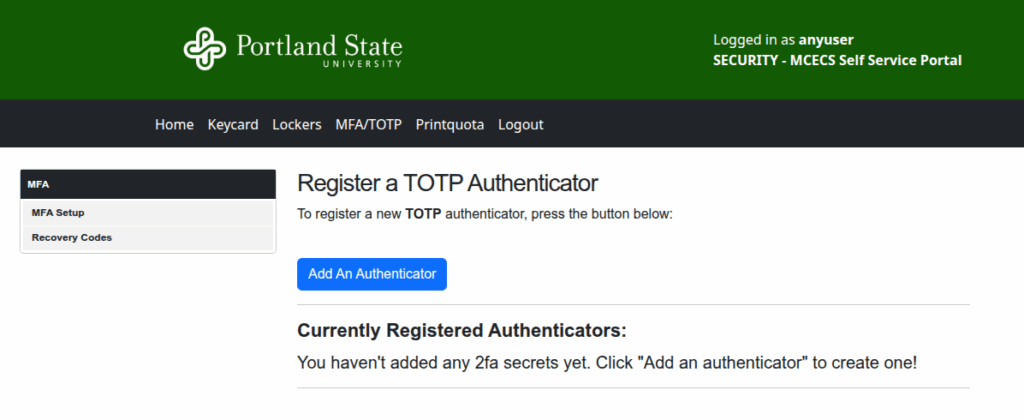
1 – Navigate to the MFA Setup Page
- Log in to the MCECS Self Service Portal
- Click on the MFA/TOTP tab at the top
- Click on MFA Setup in the sidebar
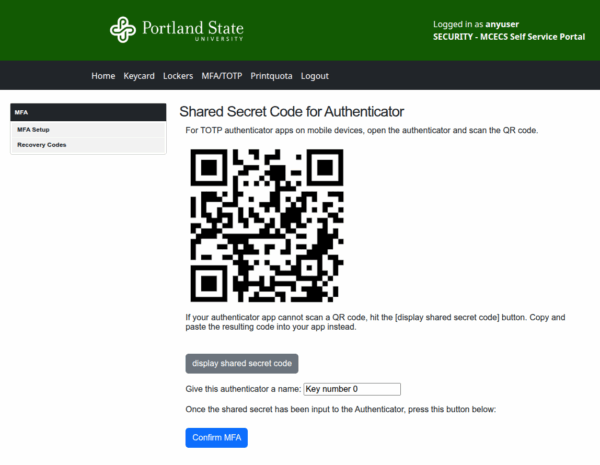
2 – Add an Authenticator
- Click Add An Authenticator
- Scan the QR code with OR manually enter the shared secret code into your preferred authenticator app
- (Optional) Give your authenticator a name so it’s easy to identify later
- Click Confirm MFA
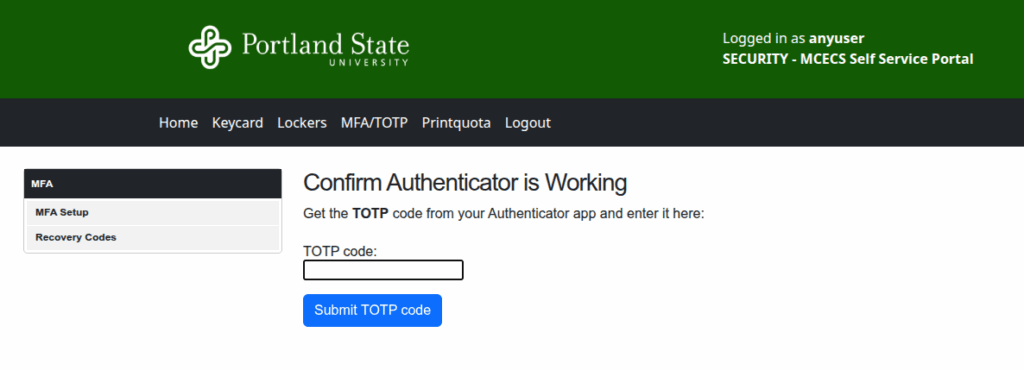
3 – Confirm Your Authenticator is Working
- Enter the TOTP code from your authenticator
- Click Submit TOTP code
Is you pass this stage, you have successfully enrolled your authenticator to our MFA system.
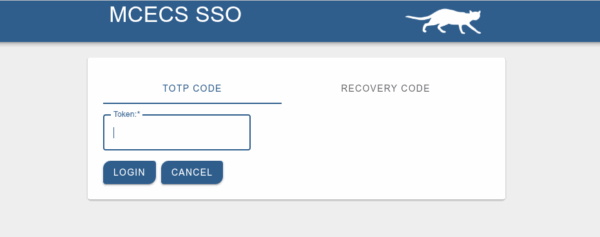
Logging In with MFA
Tip: If you use SSH keys, you can skip the TOTP prompt when connecting to Linux machines
You will be asked to provide a TOTP code upon signing in to certain MCECS services. This applies to:
- Web-based Single Sign On (SSO) logins
- Includes: Intranet, MCECS Service Portal
- SSH connections from off campus
- Applies to servers like ada, babbage, quizors, etc.
- This includes the use of SFTP and SCP
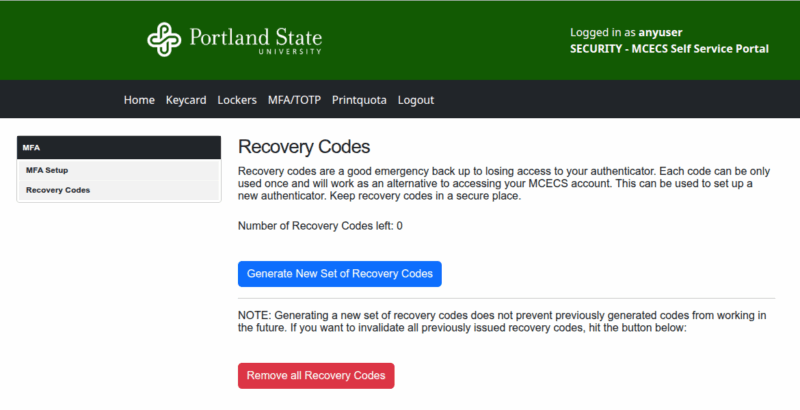
Recovery Codes
Recovery codes are one-time-use codes that let you log in without your TOTP code, which is useful if you lose access to your phone or authenticator app. Simply enter a recovery code when prompted for TOTP.
To generate a set of recovery codes:
- Log in to the MCECS Self Service Portal
- Navigate to MFA/TOTP > Recovery Codes
- Click Generate New Set of Recovery Codes
- Save the generated codes somewhere safe and secure
Locked Out of Your Account?
If you do not have access to your authenticator and need to log in, you have two options:
- If you generated and saved them, you can log in with a one-time-use recovery code
- Log in to CRAM using your Odin credentials and reset your MFA enrollment. This removes MFA from your account, allowing you to re-enroll with a different authenticator
Authentication Apps
There are many apps that can be used for TOTP authentication. You may choose whichever one your prefer. If you don’t know where to start, here’s a short list of popular options:
- DUO (mobile)
- Google Authenticator (mobile/desktop)
- Microsoft Authenticator (mobile)
- Step Two (iPhone/Mac)
- Bitwarden (mobile/desktop – also a password manager)
- KeypassXC (desktop – also a password manager)
- authenticator.cc (browser based TOTP authenticator)
Note: Duo Push is used for MFA with Odin accounts, so you may find it convenient to use Duo as your authenticator here as well